Discover how anomaly detection is used to identify unusual patterns in systems to prevent operational failures, security breaches, and attacks. Learn about detection techniques, real-world applications, and how to choose the right tools to protect your business operations.
Anomalies mean deviation from the expected patterns in data or systems, which indicate errors, breaches, or underlying problems. One of the largest data breaches in 2017 happened when Equifax had a security breach that exposed the personal information of 147 million people. Security teams had not detected unusual access patterns in their systems, so the attack remained undetected for 76 days.
Equifax subsequently spent more than $1.4 billion on settlements, fines, and remediation to rectify this oversight; this example shows how undetected anomalies directly impact business outcomes.
What is Anomaly Detection?
Anomaly detection is the process of identifying abnormal patterns, behaviors, or events that differ from the expected behavior. Such deviations can be an indication of potential fraud, security breaches, system failures, or operational failures, among other problems.
To detect anomalies, organizations train their systems to detect normal behavior and watch for outliers. This may involve reviewing data streams, logs, or transactions to identify defects that would not take place in normal scenarios.
Types of Anomalies
Anomalies can be grouped into three major categories:
1. Point Anomalies
Point anomalies occur when a single data point significantly deviates from the expected pattern in a dataset. Detecting this type of anomaly is easy because it stands out clearly from the surrounding data.
This could be an unusually large sum of money deposited into a bank account with a consistent history of small deposits.
2. Contextual Anomalies
Contextual anomalies, also called conditional anomalies, are data points that appear normal in one context but unusual in another. The data may not be abnormal, but it stands out in that specific situation.
For instance, a 300% spike in website traffic during a Black Friday sale or a major product launch is expected. But if the same surge happens on an ordinary day, it could indicate a security threat or a system glitch.
3. Collective Anomalies
A collective anomaly occurs when a collection of related data points behave differently from how they’re expected to behave. All the individual data points might look perfectly normal. However, when viewed together, they form an abnormal pattern.
For instance, a couple of unsuccessful login attempts originating from various regions may not be suspicious. However, if multiple attempts to guess the user’s password are made from multiple IP addresses in a short period, it could signal a distributed brute-force attack.
Why is Anomaly Detection Important?
Anomaly detection is an essential solution relevant to any business of any size. It can identify abnormal behavior that may indicate impending threats to an organization, allowing abnormalities to be addressed before they escalate into major problems.
Preventing Financial Loss
Security breaches, fraud, and operational disruptions can all have massive financial implications for organizations. Anomaly detection reduces financial risks by detecting unusual patterns indicating fraud, system errors, and operational failures.
Enhancing Operational Efficiency
It oversees systems and processes to identify potential problems or malfunctions before they develop into larger system failures. Addressing these issues in real-time enables businesses to smooth operations.
Cost-Effective Security Management
By prioritizing critical threats over false alarms, anomaly detection gives teams the ability to allocate resources only where they are most impactful, maximizing effort and minimizing costs. This is a way to ensure that those investments target the highest risks rather than generic threats.
Enhancing Security
It enhances security by analyzing unusual access patterns, unauthorized transactions, or malicious network activity. This analysis enables organizations to detect intact cyberattack stage and, therefore prevent breaches and damage.
Protects Integrity
Compliance and trust are key in ensuring that data is not tampered with. Anomaly detection flags unauthorized changes, unusual data access, or suspicious behavior, allowing organizations to secure sensitive data and maintain compliance with regulations.
Anomaly Detection Techniques
Statistical Methods
Statistical methods detect anomalies by analyzing data distribution and establishing a baseline for expected behavior. Any data point that is different from this expected behavior is considered an anomaly. Z-scores, Interquartile Range (IQR), and Grubbs’ test are common techniques.
Machine Learning-Based Methods
Supervised Learning: It trains models on labeled datasets so as to classify the data as normal or anomalous. It is effective for identifying known patterns but limited in discovering unknown anomalies. Decision Trees, Support Vector Machines (SVM), and Neural Networks are common techniques.
Unsupervised Learning: This method detects anomalies without labeled data by finding patterns different from the norm. It helps detect anomalies in large datasets. Examples are isolation forests, K-means clustering, and autoencoders.
Semi-supervised learning: This model uses a small amount of labeled data with a large volume of unlabelled data to detect anomalies. It balances between supervised and unsupervised pattern recognition. Examples include Self-Training Models and Variational Autoencoders (VAE)
Deep Learning-Based Methods
This method uses neural network architectures, which are effective in identifying anomalies within complex, high-dimensional data. These models automatically learn complex patterns from large datasets, which is especially useful for unstructured data, such as images, audio tapes, and sequential information.
Real-World Use Cases of Anomaly Detection
Cloud and Infrastructure Monitoring
Cloud platforms generate vast data, making tracking performance, security, and cost inefficiencies difficult. Anomaly detection recognizes unusual spikes in CPU use, memory usage, or network latency that may cause server overload or lead to imminent failures.
Solutions like Middleware handle infrastructure monitoring in real-time, providing metrics such as CPU load, request latency, and other important key metrics. This is used to create alerts for unusual behavior and helps troubleshoot performance issues.
Intrusion Detection
Intrusion detection is the identification of unauthorized access or suspicious activities that occur within a network or system. Cybercriminals exploit vulnerable systems to obtain information, interfere with operations, or gain forceful control of essential infrastructure.
Middleware is a solution for detecting anomalies that uses intrusion detection systems within its corporate network to pinpoint possible security risks. These systems improve detection by minimizing false positives, automating threat responses, and notifying security teams before any damage from attacks.
Credit Card Fraud Detection
Credit card fraud is the leading form of identity theft. It is the illegal use of a person’s credit or debit card information to purchase or withdraw money. Yearly, there are thousands of reported cases of credit card fraud worldwide.
Anomaly detection is used in this case to identify fraud by spotting unusual transaction patterns, such as sudden large purchases or activity in unexpected locations. AI-powered systems analyze real-time behavior, flagging suspicious activity to prevent financial loss.
Predictive Maintenance
Predictive maintenance, as the name implies, involves anticipating or forecasting equipment failures before they happen. This form of anomaly detection is majorly used in manufacturing, aviation, and energy industries to track equipment conditions and alert failures.
Sensors gather immediate data on temperature, vibration, and pressure, whereas machine learning algorithms assess past failures to forecast upcoming malfunctions.
While regular maintenance schedules might still be needed, predictive maintenance enhances servicing by tackling problems only when necessary, minimizing downtime and repair expenses.
Cybersecurity
Cybersecurity is a crucial issue for every organization, but cyber threats are relentless; they emerge in new shapes and forms alongside evolving trends, which makes it essential for security teams to have real-time anomaly detection capabilities.
Organizations use anomaly detection to analyze network traffic against a baseline to identify deviations from normal behavior, such as data transfers to unusual locations, communications with suspicious IP addresses, or an excessive number of failed login attempts.
Challenges in Anomaly Detection
Data Noise and High False Positive Rates
Anomaly detectors often flag normal behavior as anomalous because real-world data is noisy. This happens when models lack context, using rigid thresholds that flag normal fluctuations as anomalies. Too many false alerts create fatigue, making your team more likely to ignore real issues.
Imbalanced Datasets
Anomalies are rare, and machine learning models rely on patterns, so they struggle to detect anomalies with the few examples available. This leads to biased models that assume normal behavior is the default, making them ineffective at catching rare but critical issues.
Adaptive Learning and Model Drift
What was once an anomaly may become normal over time as new attack vectors emerge. This requires frequent updates and adaptations to maintain accurate detection. A system that flagged unusual traffic today may miss a similar pattern next week if the behavior becomes normal. Without continuous updates, models become stale, leading to missed detections and inaccurate alerts.
Algorithm Selection
No algorithm works for all types of anomalies. Choosing the wrong detection method can lead to either missing anomalies or detecting too many false ones. Finding the right balance between accuracy and efficiency is a key challenge.
Choosing a Tool for Anomaly Detection
The appropriate anomaly detection tool for your organization will depend on several factors:
Real-time Monitoring: The tool should monitor CPU usage, memory usage, network latency, and API performance to enable ongoing tracking and instant alerts for abnormal patterns.
Scalability and Performance: It must handle data volume without introducing significant delays. Simultaneously, the platform must adapt to your infrastructure requirements smoothly without declining performance.
Integration features: The tool should integrate with your current infrastructure, cloud services, and external applications to ensure continuity in your existing workflow.
Security and Compliance: Ensure that the tool adheres to industry security standards and regulations like SOC 2, HIPAA, and GDPR to safeguard sensitive information from breaches.
Anomaly Detection with Middleware
Middleware provides real-time anomaly detection via AI-powered monitoring, log analysis, automated alerts, and real user monitoring (RUM), ensuring secure, efficient, and reliable systems.
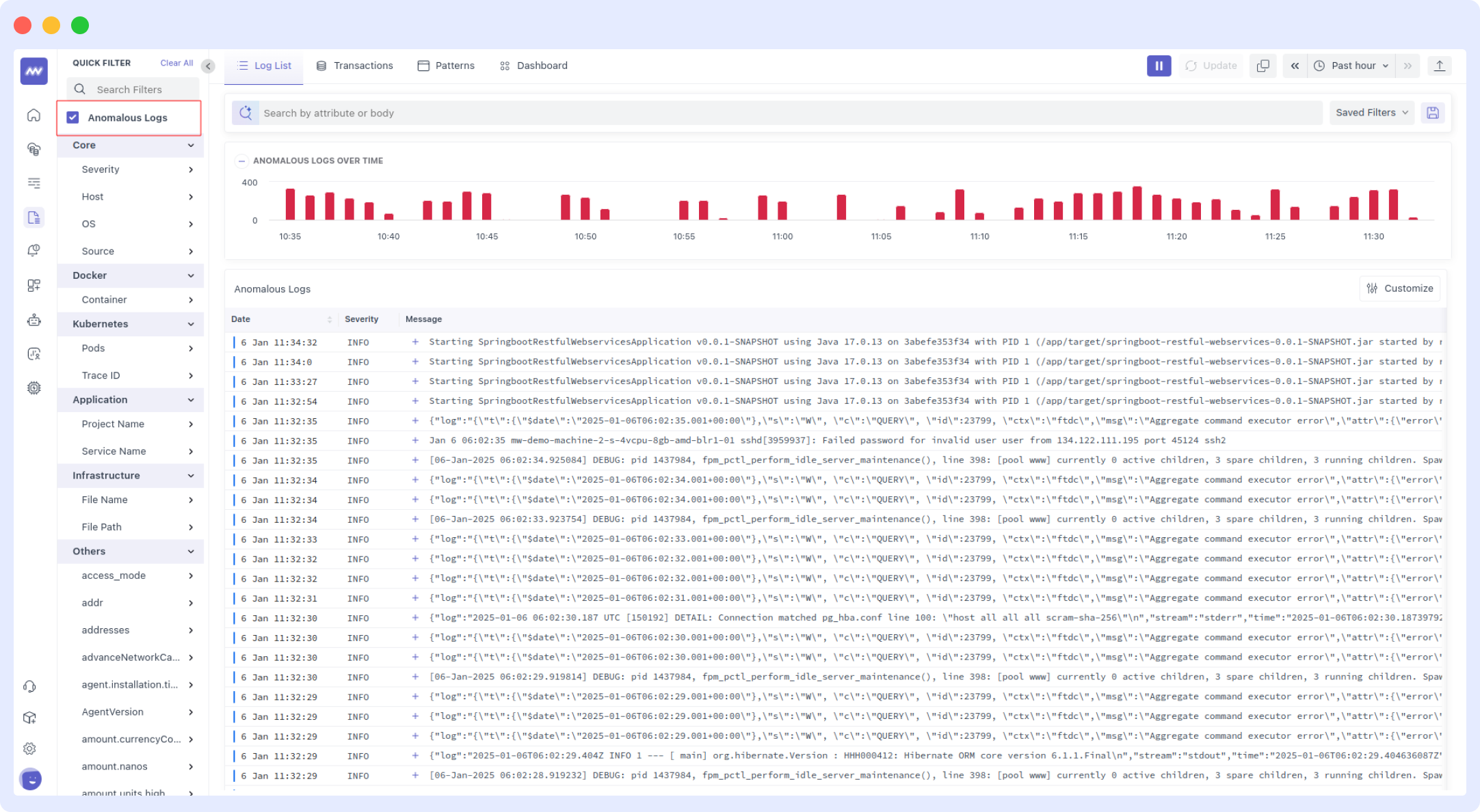
DevOps teams can track CPU surges, API performance issues, network latency, and security vulnerabilities across cloud infrastructure, applications, containers, and APIs through end-to-end observability.
The platform uses machine learning-driven log anomaly detection to identify unusual behaviors, such as unauthorized access attempts, unexpected traffic spikes, or abnormal resource usage, while adaptive baselining reduces false positives by learning normal system behavior.
Personalized alert settings enable quick responses by providing contextual insights into incidents.
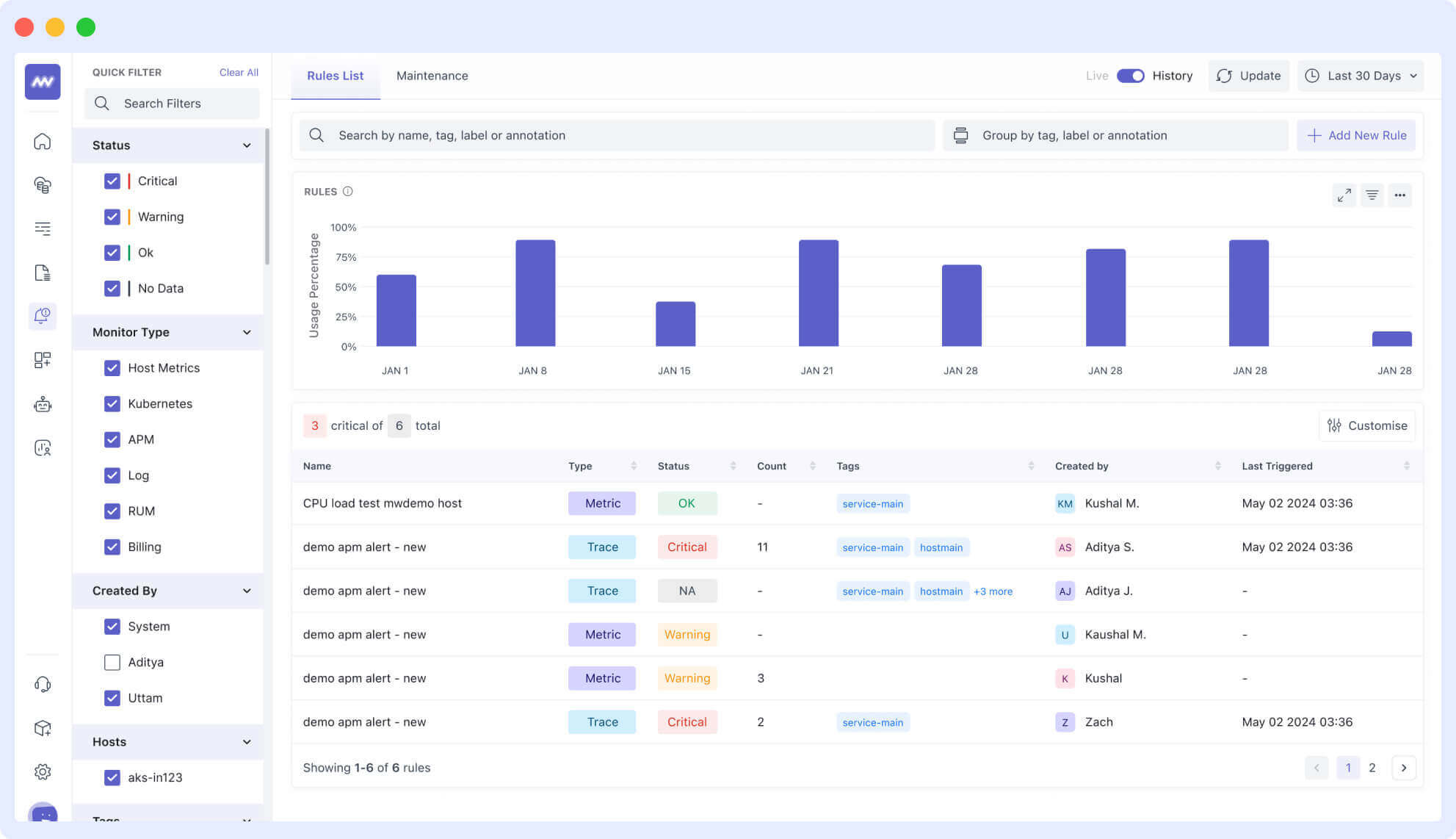
By offering session recordings and replay capabilities, the real user monitoring feature helps teams detect frontend errors, sluggish page loads, and latency problems that could impact user experience.
Middleware’s AI-powered anomaly detection allows teams to identify, analyze, and resolve issues before they escalate, maintaining smooth app performance and system stability.
FAQs
What is anomaly detection?
Anomaly detection is a term used to detect unusual data points or patterns that are different from typical behavior in a data set. Anomaly detection is applied comprehensively in system monitoring, cybersecurity, and fraud detection.
Why is anomaly detection important for business?
Prevention of financial losses, improvements in efficiency in operations, enhancement of security, preservation of data integrity, and early detection of a breach are all outcomes of this work. Those actions conserve precious time and resources.
What should I look for in an anomaly detection tool?
Real-time monitoring (e.g., CPU, latency), scalability for large data sizes, how easy it is to integrate into current infrastructure (e.g., AWS, Kubernetes), security compliance, and machine learning support.