Audit logs play an integral role in today’s specialized software development landscapes, from cloud-native applications to microservices architectures and containerized environments like Kubernetes.
Whether it’s tracking user access in multi-tenant SaaS platforms, logging configuration changes in DevOps pipelines, or monitoring database transactions in distributed systems, audit logs offer critical insights into system operations. These logs help organizations ensure compliance, diagnose issues in real time, and maintain system integrity across diverse infrastructures like CI/CD workflows, API management, and hybrid cloud platforms.
This guide dives into the essential role audit logs play in modern infrastructure, from tracking system events like user logins and data changes to providing critical insights for maintaining compliance and operational integrity. You’ll also discover how audit logs help distinguish between regular logs, monitor system development, and aid in debugging and troubleshooting.
Along the way, explore real-world use cases and common activities tracked, as well as the challenges involved in managing logs. To ensure efficient and reliable audit log management across your infrastructure, we’ll cover top best practices to keep in mind.
Understanding audit logs
An audit log tracks a sequence of activities within a system. These log events monitor everything from user actions, such as creating accounts, to system-level events, like server configuration changes.
The key components include:
- Events: Actions such as user logins, file downloads, or system updates.
- Metadata: Information about who performed the action (e.g., user ID), when it happened, and on which system or application.
- Storage & Retention: Audit logs must be securely stored for a specific retention period. For example, HIPAA requires healthcare data to be stored for 6 years.
Audit logs vs. Regular logs
While both audit logs and regular system logs capture system activity, they serve different purposes. Audit logs emphasize accountability and detect potential security incidents by recording actions like changes to access controls or unauthorized system access.
On the other hand, regular system logs are typically used for diagnosing errors and troubleshooting. For instance, a system log may note a server outage, while an audit log would capture malicious activity like an unauthorized remote shutdown or intentional data deletion.
The role of audit logs in development
Now, let’s explore how audit logs contribute to maintaining transparency and control throughout the software development process. You’ll learn how these logs can help ensure accountability, improve debugging and support compliance in your development workflows.
Ensuring code integrity
Audit logs monitor every change made during the development lifecycle. For example, if an unauthorized code change is pushed to production, the audit log can trace it back to the responsible party, ensuring quick resolution and safeguarding your codebase’s level of security.
Debugging and troubleshooting
Audit logs provide a sequential trail of events, also known as an audit trail, which helps track system changes. Acting like breadcrumbs, they allow teams to follow the exact steps leading to an issue. This detailed audit log is key to diagnosing problems in development, especially when dealing with vulnerabilities from potential threats like improper access permissions or sensitive data exposure.
In security breaches, audit trails highlight vulnerabilities—such as improper access permissions—by detailing when and how sensitive data was accessed, offering clear insights to adjust security policies and improve defenses.
Compliance and security
Audit logs are key in ensuring development processes meet regulatory compliance requirements such as GDPR or HIPAA. They track changes to user accounts or sensitive data access, ensuring organizations adhere to strict security controls and privacy regulations.
How do audit logs work?
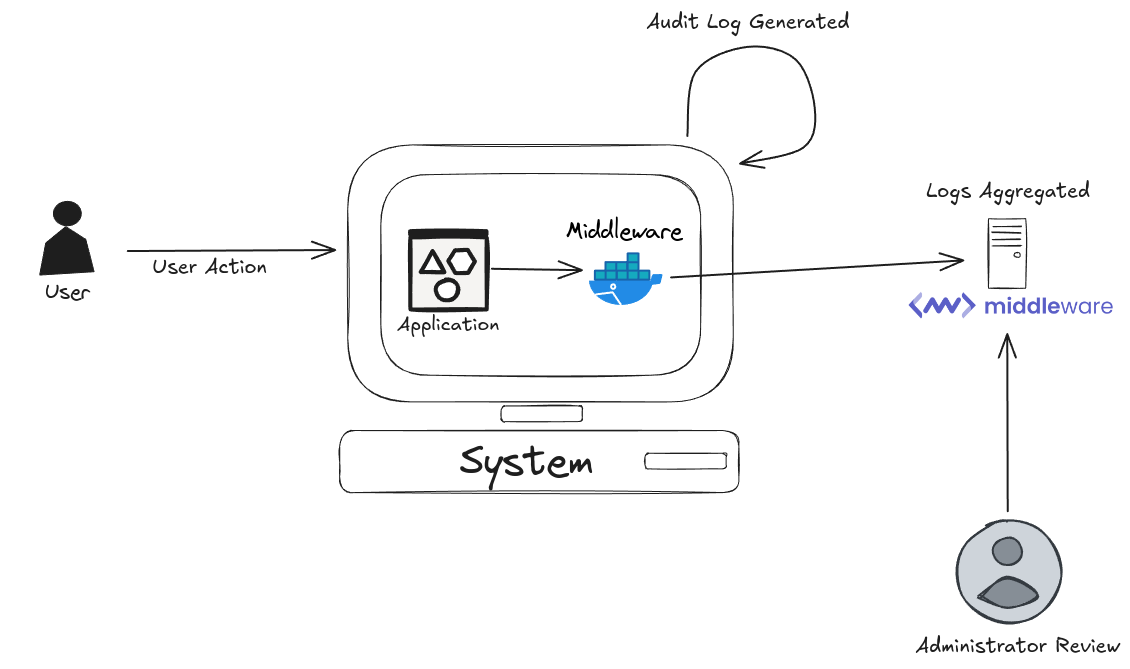
Audit logs depend on centralized log management systems to gather, store, and analyze data efficiently. The process typically involves:
- Log aggregation: Logs are collected from various sources such as applications, databases, cloud platforms, and operating systems.
- Data collection: Each log stores critical details, like event timestamps, actors (users or systems), and affected resources, making it easier for security teams to track down potential threats.
- Analysis: Once collected, logs are analyzed to detect anomalies, investigate incidents, and generate compliance reports.
For instance, AWS CloudTrail aggregates logs from resources like EC2 instances or S3 buckets, giving teams visibility into system activities and resource changes.
Common types of activity tracked by audit logs
Audit logs capture various critical activities within systems, offering insights into what actions have occurred and who initiated them. Let’s explore some common scenarios that these logs track, highlighting their importance in maintaining security controls:
- Administrative activity: Creating or deleting user accounts or changing access permissions. For example, if a user is removed from a CRM platform like Salesforce, an audit log entry will record this action, detailing the user who made the change and when it happened.
- Data access and modification: Audit logs monitor who accessed or modified sensitive information. For instance, viewing or altering payroll details in a platform like Workday would generate a log entry showing the user, time of access, and the specific data changed.
- Login failures and user denials: Failed login attempts are logged to alert administrators to potential security events like unauthorized access attempts.
- System-wide changes: Changes to infrastructure, like creating virtual machines (VMs) or deploying new services on cloud platforms such as Google Cloud, are recorded in audit logs. This helps teams maintain oversight of critical infrastructure adjustments.
Benefits of audit logging
Audit logs serve as a vital tool for maintaining the integrity, security, and reliability of your systems. By providing a record of events, they help organizations meet regulatory compliance, troubleshoot issues, and protect against threats. Below are some key benefits of effective audit logging:
- Ensuring compliance: Audit logs provide proof that systems adhere to regulatory standards, such as PCI DSS or SOC 2, which are set by industry authorities or internal controls. They ensure that your system meets the required benchmarks for handling sensitive data and security.
- Incident reconstruction: When a security incident or outage occurs, audit logs help trace the series of events leading up to the incident. For instance, after a security breach, the logs can identify which user accessed the compromised system when it happened and what actions were taken.
- Operational troubleshooting: Audit logs allow teams to identify the root cause of system failures, offering transparency and real-time monitoring to avoid future breakdowns. For example, if a critical service like a payment gateway or database goes down, these logs will reveal whether it was caused by an internal error or manual action from a user.
- Providing verifiable evidence: Audit logs can serve as reliable documentation during internal reviews, especially in high-stakes environments where log files are crucial for maintaining trust and operational efficiency. For example, logs can confirm the exact time and user who authorized a transaction or performed critical system updates, offering transparency in high-stakes environments.
Real world use cases for audit logs
Now, let’s explore some real-world applications where audit logs play an essential role in helping companies across various industries:
- In security monitoring, audit logs provide real-time insights into system activity. By tracking every login attempt and access to internal resources, they help security teams detect unusual patterns or unauthorized access, allowing for timely intervention and prevention.
- In regulated industries like healthcare and finance, these logs are vital for compliance with laws such as GDPR and HIPAA. They ensure every access to sensitive data is recorded, enabling businesses to provide clear, reliable records during audits, ensuring adherence to strict standards.
- For operational troubleshooting in cloud-based infrastructures, audit logs capture downtime, service modifications, and misconfigurations across distributed systems. This visibility helps engineers quickly identify performance issues and maintain system stability.
- In DevOps and continuous delivery pipelines, these logs help track code deployments and system changes. By recording each modification, teams can trace back to the exact point of failure, accelerating troubleshooting and ensuring code integrity throughout development.
By adopting audit logs, businesses can strengthen system oversight, boost security, and streamline regulatory compliance.
Challenges in audit logging
Over-logging and under-logging
Collecting too many logs can strain storage and processing resources, but logging too little leaves gaps in event tracking. For example, logging every API call could generate excessive data, while missing failed login attempts may overlook potential security threats.
Security concerns
Sensitive details, like access keys or passwords, should be carefully excluded from logs. For instance, logging plain-text credentials exposes security risks if an attacker gains unauthorized access to these logs.
Log correlation challenges
In distributed systems, connecting logs from different services can be difficult. For example, if a database modification triggers multiple processes across microservices like an AWS Lambda function or S3 bucket update, tracing these linked events becomes a complex task without proper log correlation tools.
Top 5 best practices for audit log management
Effectively managing audit logs is essential for tracking system activity, meeting compliance, and addressing potential risks. Below are five best practices that help manage logs efficiently and tackle key challenges like data integrity & access control.
Set retention policies
Establish a precise retention period for audit logs based on regulatory guidelines and organizational needs. For example, GDPR mandates keeping logs for 5 to 7 years. Setting appropriate retention periods ensures logs are available for future audits while preventing excess data accumulation, which can lead to storage overload and higher costs. This practice also helps avoid the risk of deleting important logs too early or keeping irrelevant data for too long.
Ensure immutability
Store logs in a tamper-proof format to prevent unauthorized changes using encryption or advanced methods like blockchain. Logs should remain unaltered from the moment they are created to maintain integrity. If logs are tampered with, their credibility is lost, undermining your ability to track events accurately, especially during audits or investigations.
Centralized log management
Instead of scattering logs across different platforms and systems, use a centralized log management solution. Collecting logs from multiple sources—such as applications, cloud platforms, and servers—into a single location enables quicker searching, correlation, and analysis. This centralization also simplifies monitoring and reporting across complex, distributed systems.
Regular monitoring
Consistently monitor audit logs to detect anomalies, unusual access patterns, or suspicious activity before they escalate into serious security breaches. Using observability tools like Middleware, you can monitor these logs in real time and receive alerts to quickly resolve issues before they escalate.
Implement access control
Limit who can view or modify audit logs to prevent misuse. You minimize the risk of internal tampering or accidental deletions by restricting access to key personnel, such as administrators. For example, sensitive logs containing user activity or critical system changes should be off-limits to unauthorized users.
Final thoughts
As audit logs evolve, they have become indispensable in managing complex systems, not only for tracking issues but also for gaining deeper insights through real-time monitoring and advanced log audits. New trends like AI-driven anomaly detection are helping organizations proactively identify potential threats, while cloud-native logging solutions simplify the management of distributed systems.
With the expansion of infrastructure, it’s essential to adopt audit logs in combination with modern observability tools. This approach ensures compliance is consistently met, debugging becomes more efficient, and system operations remain transparent.
As organizations evolve, these tools provide clear insights into system behaviors, allowing teams to resolve issues quickly and maintain control over complex environments. Now is the ideal time to integrate these practices to reinforce your system’s reliability and adaptability.
What is an audit log?
An audit log is a detailed record of system activities, capturing events like user actions or system changes. It helps track who did what, when, and where in a system, making it crucial for accountability and troubleshooting.
What should be included in an audit log?
An audit log typically includes the event name, timestamp, the actor (e.g., user or service), and details about the impacted system, offering a clear trail of actions.
What are the two types of audit logs?
Audit logs often fall into two main categories: system logs, which track technical operations, and security logs, which focus on access control and sensitive actions.
What is the difference between audit logs and activity logs?
While audit logs emphasize security and compliance, activity logs track broader user behavior without necessarily meeting strict regulatory requirements.